Jizhida's domestically produced encrypted domain supervision system solution
Overview: The Secret Domain Monitoring and Management (Secret Domain Supervision) system is a smart, intelligent, automated, and green energy-saving solution that utilizes IoT technology, audio and video transcoding technology, video AI detection technology, automatic sensing technology, control technology, and digital twin technology to achieve the integration of video monitoring, facility IoT, and AI detection in sensitive areas.
The main solution of the encrypted domain supervision system is to
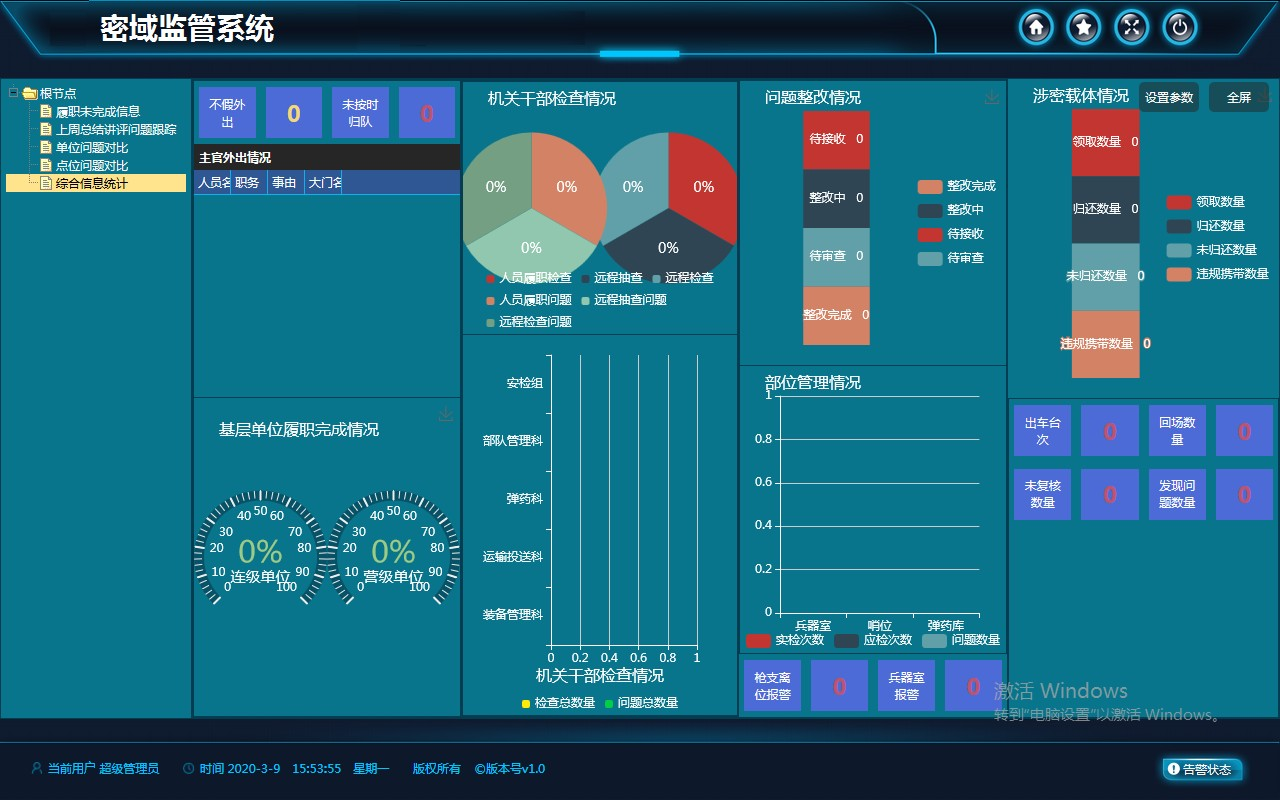
1. High definition video surveillance, facility and equipment operation status monitoring, and remote control in sensitive areas;
2. AI detection of human violations in sensitive areas (artificial intelligence), specifically prohibited behaviors within the area (such as using mobile phones, taking photos, smoking, trespassing, coercion, etc., generated through real-time AI detection of video images);
3. Facility start stop planning and AI event linkage (such as key facility activation and shutdown strictly following AI detection event driven or planned start stop scheduling to ensure strict control of facility equipment operation);
4. Automatic unmanned detection (detecting that there is no one within the set time, automatically executing unmanned strategies (such as automatically shutting down critical facilities), physically eliminating safety hazards, and greatly avoiding energy waste);
5. Voice based facility control and strategy execution (daily work (such as meetings, duty, office, production, etc.) can be controlled through voice control of facility equipment or initiation of the entire control plan);
6. Business appointments (such as meeting appointments, shift management, etc.);
7. Transaction plan (such as automatic activation of facilities and associated detection items in conference mode; start stop facilities and associated detection items in shift handover mode; automatic shutdown of facilities in unmanned mode, etc.);
8. Paperless closed-loop control (classified and stored through log recording (such as videos, pictures, alarms, equipment start stop, etc.), supporting full closed-loop log and record query, analysis, comparison, download, export, etc.).
scope of application
This system is suitable for places with high confidentiality and strict regulatory requirements, such as classified areas, classified buildings, confidential conference rooms, command centers, monitoring rooms, duty rooms, caves, equipment warehouses, workshops, and stations.
Program Features
The chip is autonomous and controllable. A hardware platform built with Feiteng, Haiguang, and Loongson processors as the core, based on LINUX/Kirin open-source software and middleware, meeting the requirements;
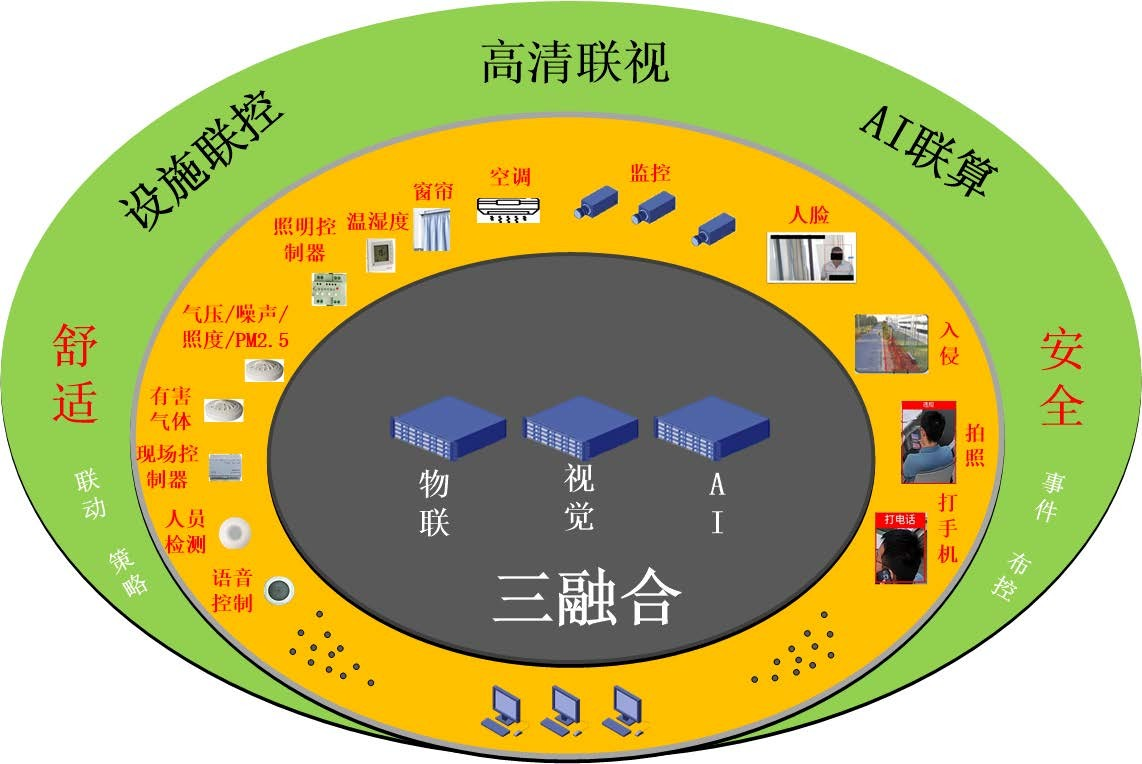
Integration of video, visual AI, and IoT; Standard end, edge, cloud B/S architecture;
Video, image, AI event, IoT point alarm, facility and equipment automation, intelligent joint procurement and control;
AI algorithm cluster (smoking, taking photos, using mobile phones, intrusion, perimeter, leaving, losing, coercion) options, rich peripheral (power distribution, access control equipment, fire control host, alarm host, air conditioning, curtains, lighting, UPS, power distribution box, temperature and humidity, harmful gases, dust, noise, light intensity, PM2.5, air pressure, wind direction, water leakage and other environmental peripheral options) options;
Support both on-site and cloud based dual control, with on-site control supporting customized voice entry and network interruption not affecting on-site control;
Alarm record recording, video, image, and recording height synthesis, easy to retrieve and query without tags.
Scheme Introduction
system composition
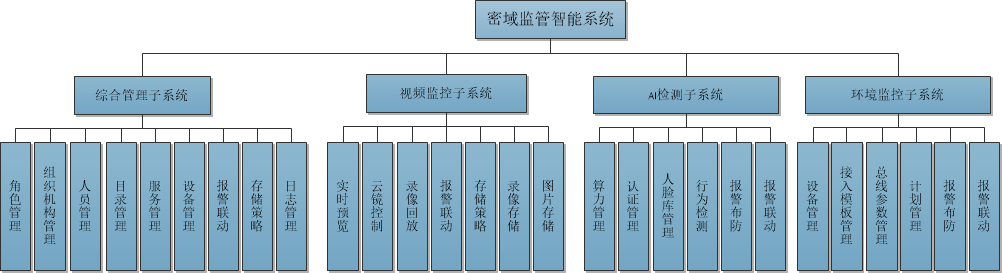
The "Secret Domain Supervision System" includes four subsystems: "Comprehensive Management Subsystem", "Video Surveillance Subsystem", "AI Detection Subsystem", and "Environmental Monitoring Subsystem". The system adopts a pure B/S architecture, and all backend systems and subsystems use C/C++development language. The human-computer interaction is developed using pure JAVA language.
The system adopts a modular structure design, supporting the allocation of various resources, links, policies, and permissions according to resources and needs. The system adopts a 20 bit unified resource code to control permissions, linkage relationships, and event traceability.
System Architecture
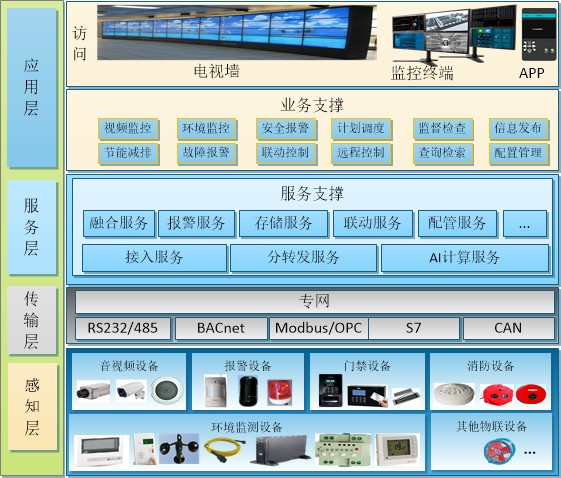
scheme
Autonomous and controllable
This system can be deployed on a general hardware platform, with independently controllable software and hardware platforms such as databases.
The system supports controllable hardware platforms such as Haiguang, Feiteng, Loongson, Shenwei, etc;
The system supports controllable operating systems, such as Zhongbiao Qilin, Galaxy Qilin, Tongxin and other operating systems;
The system supports controllable databases such as Dameng, Jincang, Nanda General, and open-source databases.
portability
All internal services and functional modules of the system can be ported to hardware platforms such as Feiteng, Loongson, and Shenwei.
Multi system integration
It can integrate multiple systems such as access control system, monitoring system, video conferencing system, alarm system, control system, environmental monitoring system, and other IoT systems into a unified and organic whole, which is conducive to breaking down information silos.
compatibility
The system has high compatibility with front-end devices and can be compatible with most mainstream manufacturers' devices on the market, making it easy for different brands of front-end products to be compatible and use, and to leverage their own technology and performance. When upgrading and renovating systems and equipment, it can effectively reduce the cost of upgrading and renovating.
High reliability
The reliability of the system is mainly reflected in the high degree of IoT integration throughout the entire system, high modularity, independent processes of each module, and no overflow of individual module anomalies; On the other hand, the system is designed with high redundancy dual control, which ensures the normal operation of on-site facilities as long as there is no power outage on site under working conditions such as network disconnection and local power failure.
Universal Strong
The system mainly adopts GB28181 ONVIF、SIP、H.323 , The overall architecture adopts B/S, and most important information or events such as alarms are pushed to the outside through WebSocket, which facilitates wider interconnection and intercommunication between different products and heterogeneous platforms.
Typical application scenarios
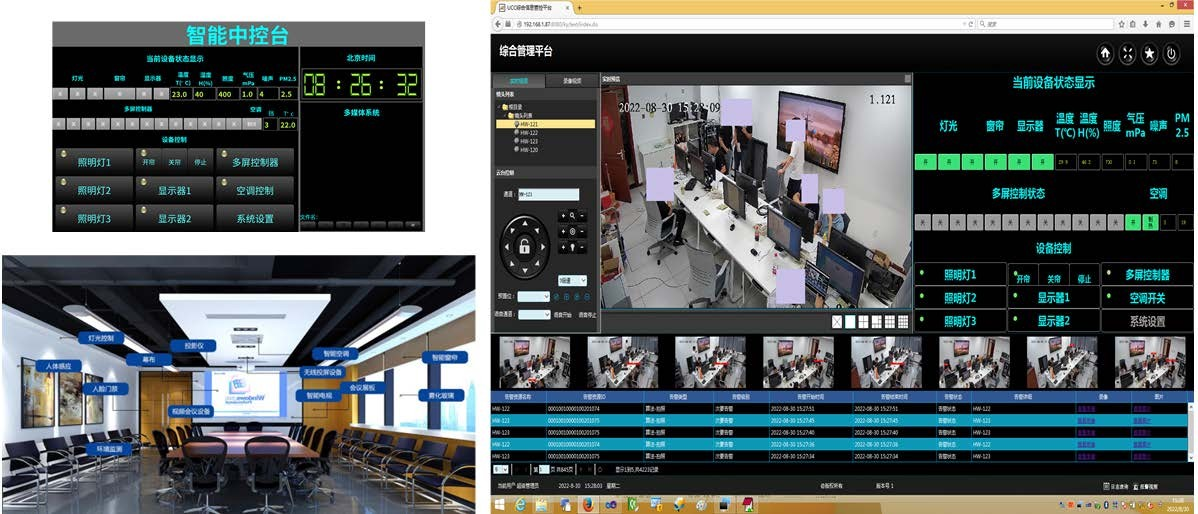
Construction content
1. Confidential conference room with high-definition video surveillance without blind spots;
2. AI real-time detection of prohibited behaviors such as smoking, taking photos, and using mobile phones;
3. Intelligent construction of conference room environment.
A、 More than 10 environmental operation plan modes, with configurable plans;
B、 The conference mode allows for scheduling of external device start and stop;
C、 Custom peripheral start stop for commuting mode;
D、 Lighting and curtains can be adaptively and intelligently scheduled and controlled according to the intensity of light;
E、 The air conditioner can adaptively and intelligently schedule control based on real-time temperature and humidity indicators;
F、 Can support user-defined batch and automated linkage control;
G、 Switchable seat computer screen projection;
H、 Automatically detect incoming people and activate basic facilities;
I、 Automatically detect no one, automatically shut down facilities after timeout, and eliminate safety hazards;
J、 Indoor facilities can be voice controlled, without the need for leaving or remote control;
K、 Indoor facilities can be remotely controlled.
4. Alarm record recording, image synthesis, query and retrieval.
significance
1. Monitoring without blind spots;
2. Real time detection, real-time alarm, and video image synthesis recording of violations;
3. Standardized and planned conference environment management, ensuring safety and efficiency;
4. Intelligent, automated, and voice based control of facilities and equipment, providing comfort, safety, and efficiency;
5. Key facilities are shut down when unmanned to eliminate safety hazards;
6. Facilities and equipment can be remotely controlled.
Cave Depot

Construction content
1. High definition video surveillance with no blind spots in the cave;
2. AI real-time detection of prohibited behaviors such as smoking, taking photos, using mobile phones, trespassing, and coercion;
3. Personnel/vehicle access control/gate/vehicle management for entering and exiting the cave;
4. Fire alarm management;
5. Equipment and material inventory management;
6. Intelligent construction of cave environment.
A、 More than 10 environmental operation plan modes, with configurable plans;
B、 Storage mode can be set for peripheral operation;
C、 Customize the start and stop of external devices in the on/off duty mode;
D、 The lighting can be adaptively and intelligently scheduled and controlled according to the intensity of light;
E、 The air conditioner can adaptively and intelligently schedule control based on real-time temperature and humidity indicators;
F、 Ventilation can be controlled through adaptive intelligent scheduling based on toxic gas indicators;
G、 Can support user-defined batch and automated linkage control;
H、 Automatically detect incoming people and activate basic facilities;
I、 Automatically detect no one, automatically shut down facilities after timeout, and eliminate safety hazards;
J、 The facilities in the warehouse can be voice controlled without leaving the post, personnel leaving their positions, or remote control;
K、 The facilities inside the warehouse can be remotely controlled.
7. Alarm record recording, image synthesis, query and retrieval.
significance
1. Cave monitoring has no blind spots;
2. Real time detection, real-time alarm, and video image synthesis recording of violations;
3. Standardized and planned management of cave environment;
4. Intelligent, automated, and voice based control of facilities and equipment, providing comfort, safety, and efficiency;
5. Key facilities are shut down when unmanned to eliminate safety hazards;
6. Facilities and equipment can be remotely controlled.
laboratory
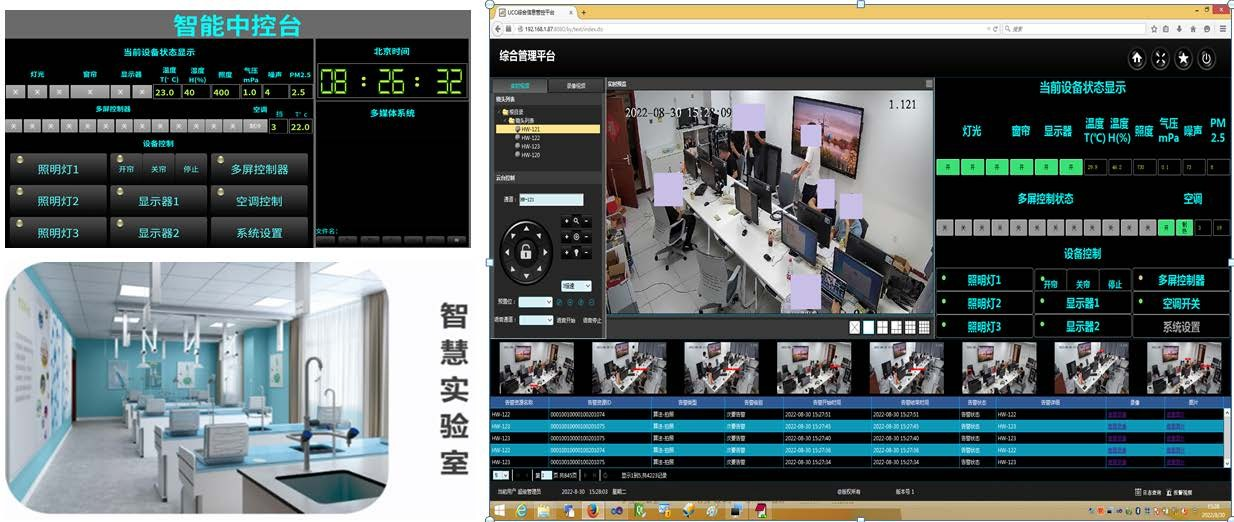
Construction content
1. High definition video surveillance without blind spots in the laboratory;
2. AI real-time detection of prohibited behaviors such as smoking, taking photos, and using mobile phones;
3. Intelligent construction of laboratory environment.
A、 More than 10 environmental operation plan modes, with configurable plans;
B、 Custom peripheral start stop for commuting mode;
C、 Lighting and curtains can be adaptively and intelligently scheduled and controlled according to the intensity of light;
D、 The air conditioner can adaptively and intelligently schedule control based on real-time temperature and humidity indicators;
E、 Can support user-defined batch and automated linkage control;
F、 Switchable seat computer screen projection;
G、 Automatically detect incoming people and activate basic facilities;
H、 Automatically detect no one, automatically shut down facilities after timeout, and eliminate safety hazards;
I、 Indoor facilities can be voice controlled, without the need for leaving or remote control;
J、 Indoor facilities can be remotely controlled.
4. Alarm record recording, image synthesis, query and retrieval.
significance
Monitoring without blind spots;
Real time detection, real-time alarm, and video image synthesis recording of violations;
Standardized and planned management of experimental environment;
Intelligent, automated, and voice based control of facilities and equipment, providing comfort, safety, and efficiency;
Key facilities are shut down when unmanned to eliminate safety hazards;
Facilities and equipment can be remotely controlled.
operating room

Construction content
1. Medical gas monitoring (oxygen, laughing gas, nitrogen, carbon dioxide, argon, compressed air, etc.);
2. Air conditioning system monitoring (check-in, temperature and humidity, positive pressure values, air conditioning system faults, blockages, positive and negative pressure alarms, positive and negative pressure exhaust fan lights, etc.);
3. Lighting fixtures, surgical table lamps, and auxiliary light controls;
4. Exhaust emission control and status;
5. Fire alarm monitoring;
6. IT power alarm status monitoring;
7. Accurate timing for surgery, including positive timing and countdown;
8. Telephone system and multimedia;
9. Reporting, pushing, receiving, processing, verifying, and querying faults and work orders;
10. Support remote monitoring through mobile apps.
significance
1. Automated and intelligent monitoring of all elements of cleanliness in operating rooms;
2. Integrated touch control operating room facilities and equipment (such as surgical table lamps, air conditioning check-in, positive and negative pressure settings, temperature settings, exhaust emissions, alarm elimination, telephone dialing, etc.);
3. Accuracy and real-time monitoring of operating room environmental indicators;
4. Fault and work order automation, paperless, traceable records;
5. Remote monitoring is possible, saving a lot of time for medical staff and maintenance personnel.
System hardware product selection
Based on the Haiguang processor platform product
Jizhida is equipped with Haiguang No.2 CPU and subsequent Haiguang No.3 CPU, supporting trusted computing and 1U/2U whole machine platform products.
GNS-1411

◆ Supports Haiguang No.2 CPU and subsequent Haiguang No.3 CPUs
◆ Support trusted computing
◆ Reserved SODIMM DDR4 slot for expanding IPMI functionality
The platform has high computing performance, high internal bandwidth, and high I/O bandwidth, and is widely used
A complete ecological chain that can support domestic or open-source systems
GNS-1413

◆ Supports Haiguang No.2 CPU and subsequent Haiguang No.3 CPUs
◆ Support on-chip trusted computing
◆ Onboard 8GB electrical and 4GB optical interfaces
◆ Onboard 4 DDR4 UDIMM slots, capable of up to 128GB of memory capacity
◆ Comprehensive ecological chain, supporting domestic or open-source systems
GNS-141A

◆ Supports Haiguang No.2 CPU and subsequent Haiguang No.3 CPUs
◆ Built in 1 TPM card interface to achieve security and trustworthiness
◆ Onboard 2 Gigabit RJ45 management interface, supporting 4/8 front-end expansion network card modules
◆ Onboard 4 DDR4 UDIMM slots, capable of up to 128GB of memory capacity
The platform has high computing power, high I/O bandwidth, wide applications, good portability, and good compatibility
GNS-1421

◆ x86 platform, supporting Haiguang 3 5/7 series CPUs
◆ CPU integrated security chip, capable of meeting the requirements of protection 2.0
◆ Supports 2U 4/8 expansion network card interface, or 4 expansion network cards and 4 hard drives
◆ High bandwidth expansion slots for upper and lower layers, fully expanding the performance of network cards
◆ Rich IO interfaces for flexible selection and matching
◆ High computing performance, high memory bandwidth
Products based on the Feiteng processor platform
GNS-1302

Feiteng 4-core or 8-core CPU, providing high IPC and supporting hardware virtualization
◆ NetEase network card chip,
UEFI, firmware architecture, secure and controllable, integrated secure and trusted solutions
◆ Support localization of operating systems
◆ Supports trustworthy Huatai cards and security software, supports TPCM TCM1.0、TPM2.0, Support active measurement, support SM2/SM3/SM4 algorithms, etc., meet the requirements of equal protection 2.0